Protection scene

Analyzing Unknown Attacks
Rule-based security products cannot detect unknown threats, but the system can detect unknown attacks, allowing enterprises to adjust security policies to reduce security risks.

Intrusion Forensics
Identifying the files and tools uploaded by attackers through the record of attack process and the the characteristics of attack traffic packets, then analyze data threat intelligence resources to trace the source of the attacker.

Malicious Code Detection
Capture network attack traffic and malicious attack codes and identify attackers' intentions by analyzing malicious codes.

Attack & Defense Drill
The system can detect attacks and capture intrusion traffic to facilitate the defense side in red-blue confrontation within the enterprise or a large-scale network protection scenario
Malicious Code Detection.
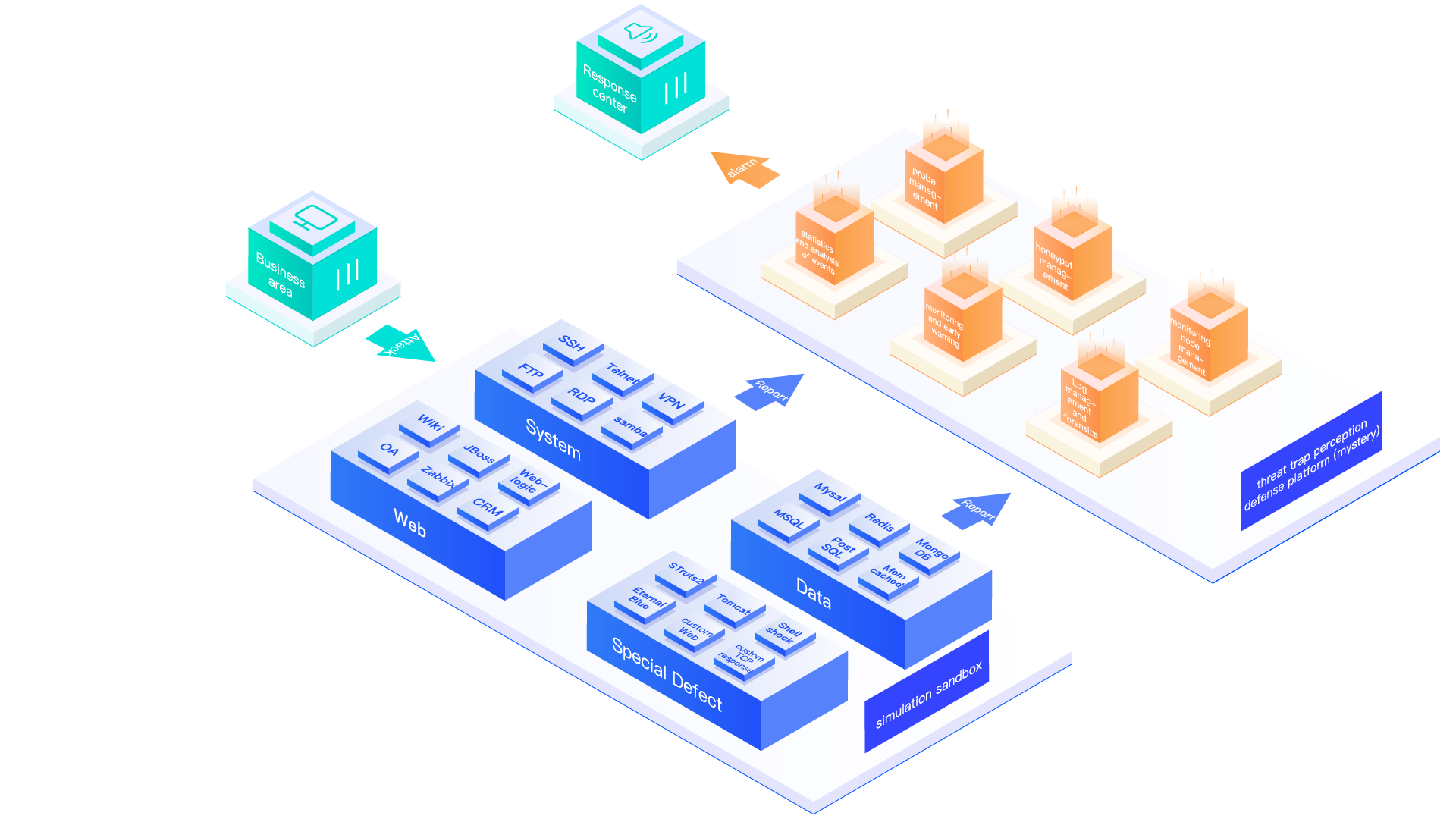

Product Advantages
Address:6th Floor, Yinke Building, 38 Haidian Street, Haidian District, Beijing
Beijing Starcross Technology Co., LTD. Beijing ICP prepared No.19053406
Success!